Extension Security Design
We mentioned extension password managers are not safe enough in our previous post Stop using browser extension password managers. Use password manager extension instead.
Talk is cheap. Show me the video.
We injected a piece of "bad code" into a Github page with no login form, and stole the password by tricking the user into closing an ugly ads. (The opacity of Login form and LastPass can be very low to be imperceptible in real attack.)
The demonstration exploited LastPass password manager without any vulnerability. A real attack might be able to steal passwords with zero-click if some proper vulnerabilities are available.
Most web pages contain lots of third party contents and codes, especially ads. It is almost impossible to ensure all of them are risk-free. Extension password managers can be pretty vulnerable.
Requirement
Since long ago, ID Guard Offline users have been asking for bringing our advanced security features to Windows. It is not easy. We have done lots of research for possible solutions.
Desktops do not have full sandbox protection. Persistent data of apps can be easily accessed by malicious programs which can even obtain the master passwords of password managers by Keylogger or scanning runtime memory. What's more, without security chip, desktops cannot keep the encryption keys for password managers as secure as modern mobile system.
Last year, a research from Independent Security Evaluators, Password Managers: Under the Hood of Secrets Management,was reported by Washington post Password managers have a security flaw. But you should still use one..
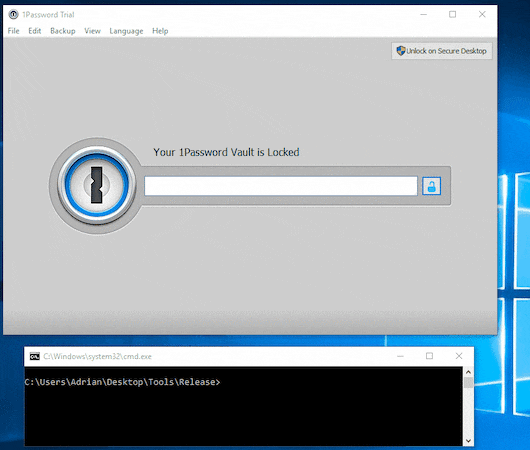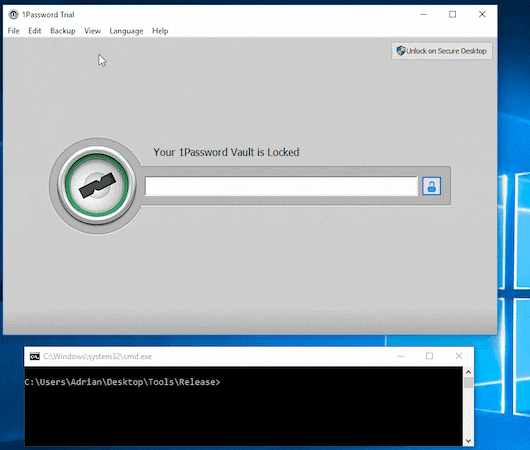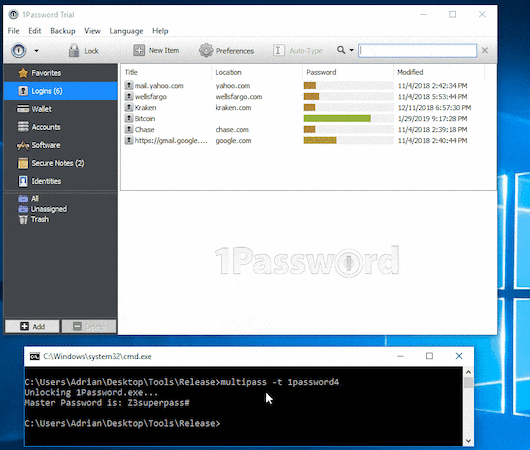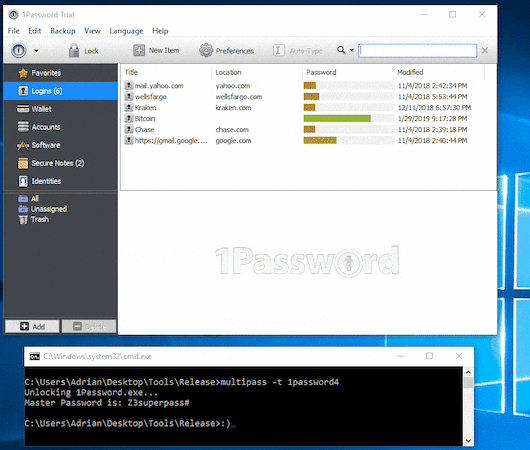
Master password of 1Password extracted by Adrian Bednarek
There are two types of password managers on desktops:
-
Desktop app
Since about a decade ago, PBKDF2 algorithm has brought true protection to password managers. By taking advantage of PBKDF2, the second generation password managers allow user to set a master password to protect passwords. They transform the master password into a secret key and then encrypt passwords, which is still the foundation of most password managers today.
-
Extension app
Desktop apps usually remember a user's password at first time login. But web apps ask for passwords time and time again due to browser restrictions and security concerns.
Extension password managers are based on extension API of browsers and keep synchronized from cloud. They can offer password filling in browsers, as well as the same features in their desktop version. That makes them very popular.
Do not use browser built-in password managers. They are the first generation password managers. They can manage passwords but not protect them well.
We'd like to help autofill passwords in browsers, but still keep them secure. So we refused the popular extension password manager solution and designed our own secure remote fill technology.
Design
Why not another extension password manager?
Most extension password managers include these components:
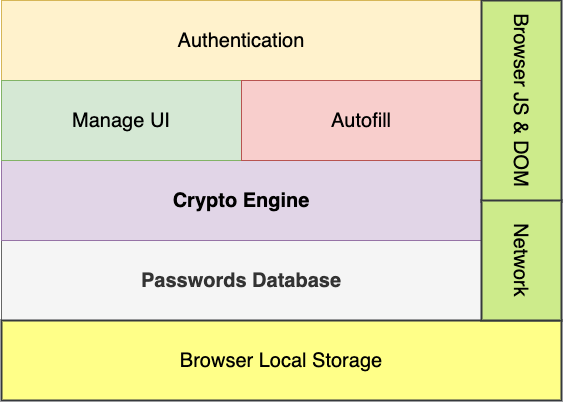
Besides the lacking of sandbox protection and security chip on desktops, compared to smartphones, extension password managers are facing more serious threats:
-
Master password is more vulnerable.
Desktop apps can use some features offered by operating system to prevent Keylogger from recording master password. But browser extensions cannot. They are restricted from accessing operating system API and totally rely on browser text input box, which cannot stop Keylogger.
-
Browser vulnerabilities
Browsers are made to surf the Internet and are the most vulnerable software. Extension password managers are more likely to be exploited remotely due to those vulnerabilities.
-
Web DOM is a fundamental attack surface.
Martin Vigo demonstrated several methods to break LastPass in Even the LastPass Will be Stolen, Deal with It!.

Extension password managers are based on Web technology, which is very open, powerful and flexible. Programs can access almost all data in a page via DOM/Javascript. Sean Cassidy, a well-known security researcher, believed that it is very difficult to eliminate risks of extension password managers.
Innovative design
Exploring
As we explored, the picture became clear.
-
Adopt browser extension API.
Extension API can help parse login form, URL, etc. and fill usernames/passwords in web page.
-
Do not manage passwords.
We agree with Sean Cassidy that Browser Extension Password Managers Should Not Be Used. So our extension does not manage passwords at all. Actually, it implements a remote autofill framework rather than a password manager. No password can be hacked.
-
How does the app get the filling information?
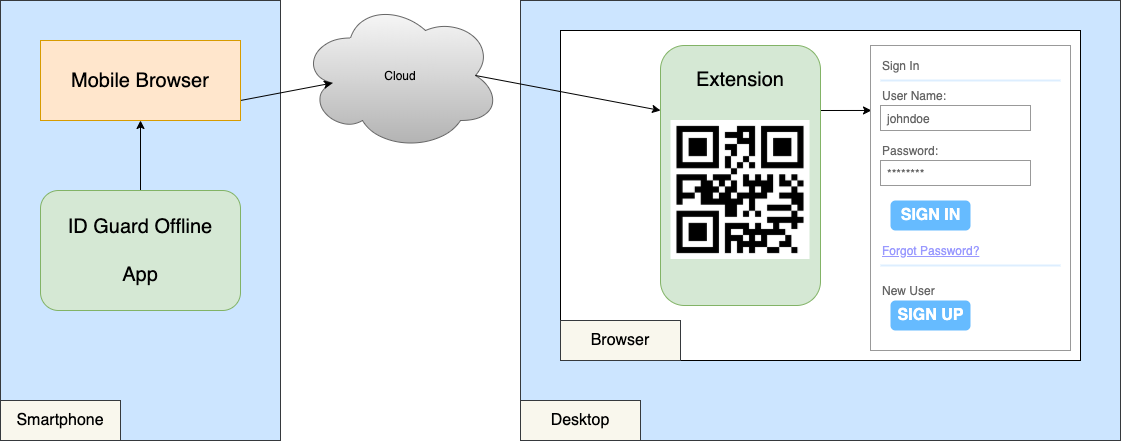
To fill passwords in web page, we can just let the extension send the filling information, i.e. which website to fill, to the app and then let the latter send the selected account password back to the former. It is quite straightforward, right? But in this case, our app must have Internet permission to communicate. We have always insisted on NO attack surface from the Internet. After quite a lot of research, a new idea came into our mind:
- The extension encodes the filling information into a QR code and shows it on the screen.
- ID Guard Offline app scans the QR code to get the filling information, WITHOUT Internet permission.
-
How does the app send password to the extension?
Again, how to do that while keeping our app offline? Yep, it is possible to scan smartphone screen by camera on desktop computers, but it hurts easy-to-use.
We can employ a mobile browser to send. ID Guard Offline app launches a mobile browser to run a web app which then sends encrypted username and password to the extension. It is simple to view source code of a web app, so anyone can audit the code to see whether it is safe.
Architecture
We explained how to use the extension in our previous post Stop using browser extension password managers. Use password manager extension instead. Here is the tech side.
Architecture Diagram
Sequence Diagram
sequenceDiagram
participant User
participant LoginPage
participant Extension
participant MobileBrowser
participant IDGuardOffline
note over Extension: make ECC key pair
Extension ->> LoginPage: 1. show QR code
User ->> IDGuardOffline: 2. scan QR code on page
note over IDGuardOffline: show matched account for page
User ->> IDGuardOffline: 3. select account
note over IDGuardOffline: make ECC key pair and make ECDH agreed secret
note over IDGuardOffline: encrypt username and password
IDGuardOffline ->> MobileBrowser: 4. encrypted data
MobileBrowser ->> Extension: 5. send via Cloud
note over Extension: make ECDH agreed secret and decrypt
Extension ->> LoginPage: 6. fill
-
ID Guard Offline extension generates an Elliptic-curve cryptography(ECC) public-private key pair if a login form is detected on the web page, and then encodes the page URL and public key into a QR code.
-
User scans the QR code with ID Guard Offline app.
-
When an account is selected, the app,
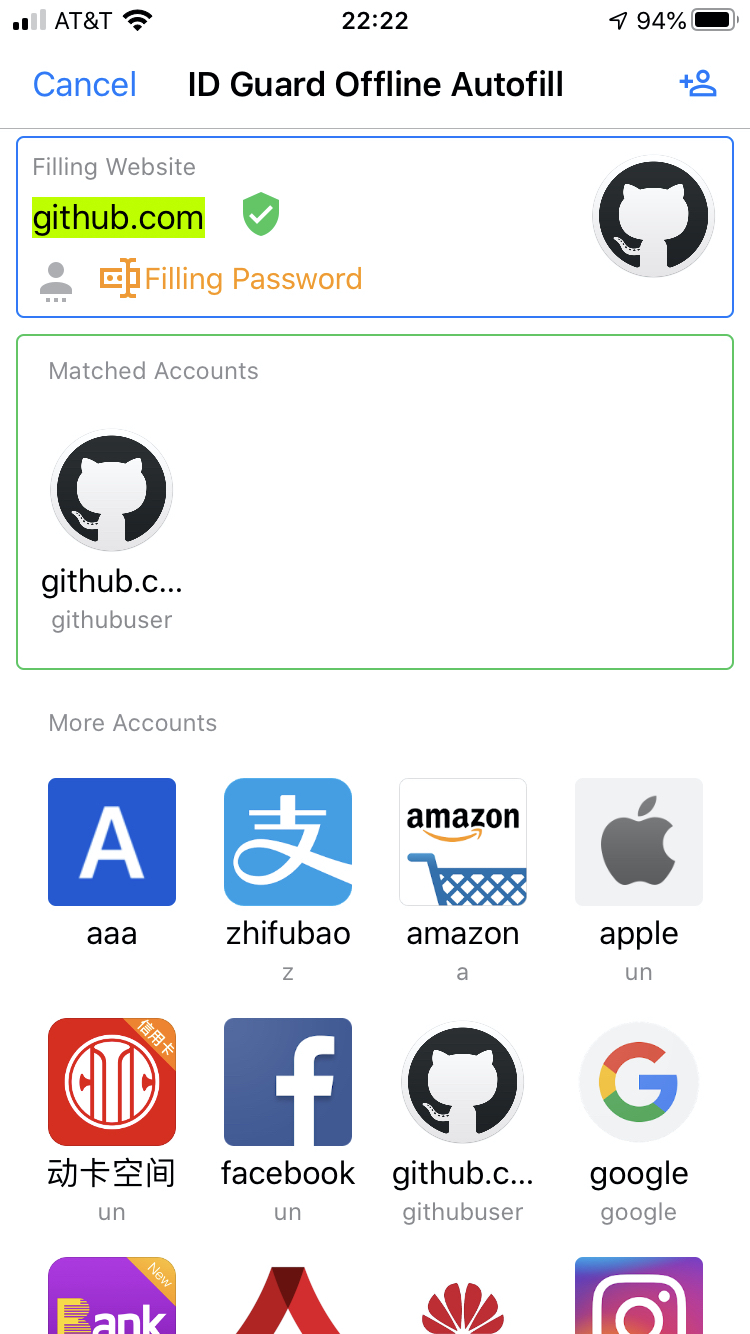
- generates an elliptic-curve public-private key pair
- generates a shared encryption key with ECDH algorithm
- encrypts username and password with the shared key
-
The app launches a mobile browser on the phone to send encrypted data to the extension.
-
The extension generates shared key with ECDH algorithm and decrypts username and password.
-
The extension fills username and password into the login form.
With the ECDH key agreement algorithm, ID Guard Offline app and extension implement an end-to-end encryption, which makes sure that passwords can never be stolen by hackers or our employees.
Since the autofill process involves user interaction - tapping on the phone, bad programs cannot steal passwords stored inside the app on the phone even if zero-click vulnerabilities of browser can be used.
Extension components
Extension architecture
Chrome extension is made up of four components:
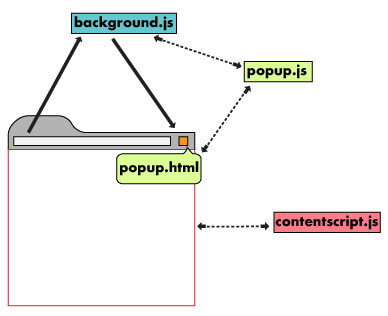
Background Scripthandles events and messages.UI Elementsincludes extension popup, menu items, etc.Content Scriptcan access contents in current web page.Options Pageallows users to set some parameters.
For security reasons, each component runs in its own process, and they can talk with each other by message passing.
The UI Elements and Options Page of ID Guard Offline extension are pretty simple. We only focus on the Content Script and the Background Script in this article.
sequenceDiagram
participant BackgroundScript
participant ContentScript
participant WebPage
participant IDGuardOffline
ContentScript ->> WebPage: detect login form
ContentScript ->> BackgroundScript: make ECC key pair
BackgroundScript ->> ContentScript: public key
ContentScript ->> WebPage: show QR code(public key)
IDGuardOffline ->> WebPage: scan QR code(by user)
note over IDGuardOffline: select account to fill(by user)
note over IDGuardOffline: make ECC key pair
note over IDGuardOffline: make shared secret key and encrypt
IDGuardOffline ->> BackgroundScript: encrypted data, public key via H5 app/cloud
note over BackgroundScript: make shared secret key and decrypt
BackgroundScript ->> ContentScript: username, password
ContentScript ->> WebPage: fill
Content Script
The Content Script parses the browsing web page to detect login form and fill username and password into the form. Besides, it offers a lot of security enhancement.
-
Passwords security
Autofill is awesome. However, it exposes an attack surface at the same time. Hackers might be able to loot passwords by abusing autofill. Checkout a recent research paper Revisiting Security Vulnerabilities in Commercial Password Managers. The author found that none of those password managers could defend all the attacks.
ID Guard Offline offers Advanced Phishing Detection that can help users identify all the threats mentioned in the paper. Furthermore, our
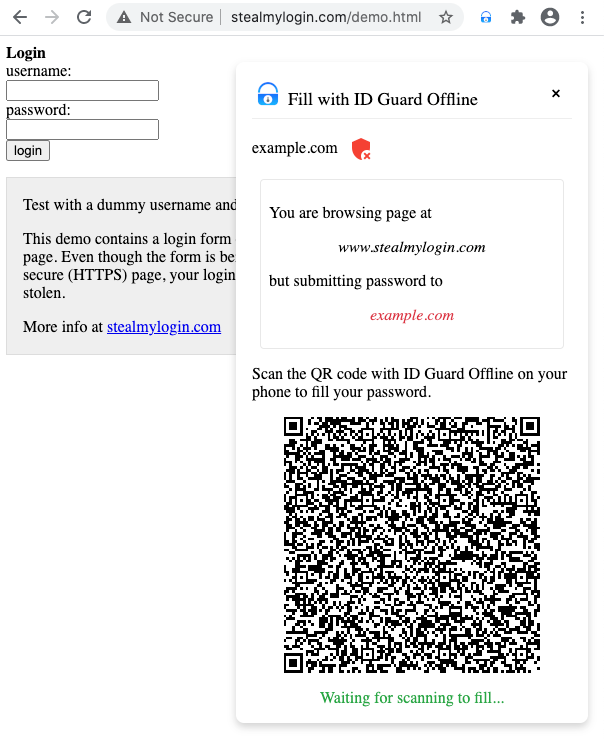
Content Scriptcan detect more risks like:- Passwords will be disclosed when submitting over HTTP connection which is not safe.
- Passwords can be stolen when current page loaded over HTTP connection.
- The login form in iframe can be hacked when the main page loaded over HTTP connection.
- Passwords are submitted to another website.
-
Minimized the attack surface
ECC is very secure for now. However, quantum computing has demonstrated the potential to break it in the future. To minimize the risk, the QR code is limited to be valid only within 2 minutes. The scan box will be closed automatically after 2 minutes, and the app will prompt a warning when an expired QR code scanned.
Users can pick up their phone to scan the QR code within 2 minutes in no hurry. We believe even quantum computers might not be able to break ECC within 2 minutes, let alone traditional computers.
Background Script
The Background Script is the core of our extension. We design a number of security enhancements.
-
Encryption keys are isolated in background script process.
The
Background Scriptmanages encryption keys and cloud communication in its own process. It offers limited service APIs via Chrome message passing toContent Script. So malicious codes running in the web page cannot access keys and cloud services via Web DOM API. -
Speed limitation
Some password managers can surrender passwords to malicious programs. One failure in their design is no speed limit. The bad program can steal passwords by simulating login requests. Our extension denies requests if the speed is abnormal.
-
Strong ECC algorithm
By implementing end-to-end encryption with ECDH key agreement algorithm, our extension encrypts and transports passwords on top of HTTPS/TLS layer. Even our employees cannot decipher user passwords. For security and compatibility, we use P-384 from WebCrypto supported curves: P-256, P-384, P-521.
-
Non-extractable private key
const curve = {name: "ECDH", namedCurve: "P-384"}; page.keyPair = await window.crypto.subtle.generateKey(curve, false, ["deriveKey"]);We set parameter
extractabletofalseto not allow extracting the private key when using theWebcryptoAPI. Given that bad programs can break into the background script, it probably can not get the private key. -
One-time key
ECC key pairs are neither saved nor reused. Whenever a new QR code is created, the extension generates a new key pair. Together with the 2-minute-limited QR code, it increases the cost of cracking tremendously. Hackers cannot break the encryption by using a previously cracked key.
After receiving the public key and encrypted data from the app, the extension recovers username and password with 2 steps.
-
Generates the shared secret key.
const curve = {name: "ECDH", namedCurve: "P-384"}; const publicKey = await window.crypto.subtle.importKey('spki', keyBytes, curve, true, []); const ecdh = {name: "ECDH", public: publicKey}; const aes = {name: "AES-GCM", length: 256}; const secretKey = await window.crypto.subtle.deriveKey(ecdh, page.keyPair.privateKey, aes, true, ["encrypt", "decrypt"]);The secret key for
AES-256-GCMis generated with the standardECDHalgorithm. -
Decrypts username and password from encrypted data.
const ivBytes = Uint8Array.from(window.atob(encrypted.iv), c => c.charCodeAt(0)); const cipherBytes = Uint8Array.from(window.atob(encrypted.cipher), c => c.charCodeAt(0)); const aesParams = {name: "AES-GCM", iv: ivBytes}; const bytes = await window.crypto.subtle.decrypt(aesParams, secretKey, cipherBytes);It parses
IV(Initial Vector)and cipher text, and then decrypts the cipher text with the secret key above.We choose
AES-256-GCMmode here because it can detect change of cipher text and is much safer, while some other modes, likeAES-CBC, cannot.
Of course, HTTPS/TLS is a must for transportation, which adds an additional layer of security.
Comparison
Most extension password managers manage and synchronize passwords with cloud service. But ours is not. The extension and the app are two separated components working together to fill passwords in browsers.
- The app keeps user passwords safe by making full use of the security features(Internet permission, sandbox protection, security chip...) available on mobile system.
- The extension implements a remote autofill framework and secures the passwords transportation over network.
The design minimizes the attack surfaces of both components and secures user data much better.
Comparison of attack surface
| Attack surface | ID Guard Offline app | ID Guard Offline extension | extension password managers |
|---|---|---|---|
| Internet permission | N | Y | Y |
| Persistent storage | Y | N | Y |
| UI | Y | Y | Y |
| Web DOM | N | Y | Y |
There are 4 attack surfaces uncovered in extension password managers, while only 2 in our app and 3 in our extension. This solution isolates 2 most risky attack surfaces, network and storage. The app stores passwords without accessing the Internet, and the extension accesses the Internet without storing any passwords.
By utilizing security chip, sandbox protection and eliminating Internet access, our app, ID Guard Offline password manager, is much much safer than extension password managers. So let's focus on the extension part and compare each attack surface.
-
Internet permission
-
Malicious codes in web pages and bad browser extensions might be able to extract passwords from extension password managers. Check it out LastPass Bug Lets Hackers Steal All Your Passwords.
-
The cloud side. Bad employees or hackers who break into the cloud can attack from cloud side. They might be able to inject bad code into service pages to extract master passwords or encryption keys when a hacked page is loaded by extension. Are you shocked that we cannot completely trust developers?
Our extension is much safer. As we know, it might be impossible to prevent all network attacks. Bad code in web pages or bad browser extensions might still be able to steal the filling password. But it is impossible to grab all passwords because they are staying safe on smartphone.
-
-
Persistent storage
Lots of programs running on Windows or other desktop OS can access data stored by Chrome, including password databases, cookies and other important data kept by extension password managers.
If a user enables remembering master password, bad programs can decrypt all passwords just like the extension password manager. If not, the master password is the only obstacle. Though master passwords must be unique, complex and long, lots of users still use weak passwords or reuse them. And more, master passwords can be recorded by
Keyloggers.Of course, it is still safer than Chrome's built-in password manager which does not require a master password, nonetheless.
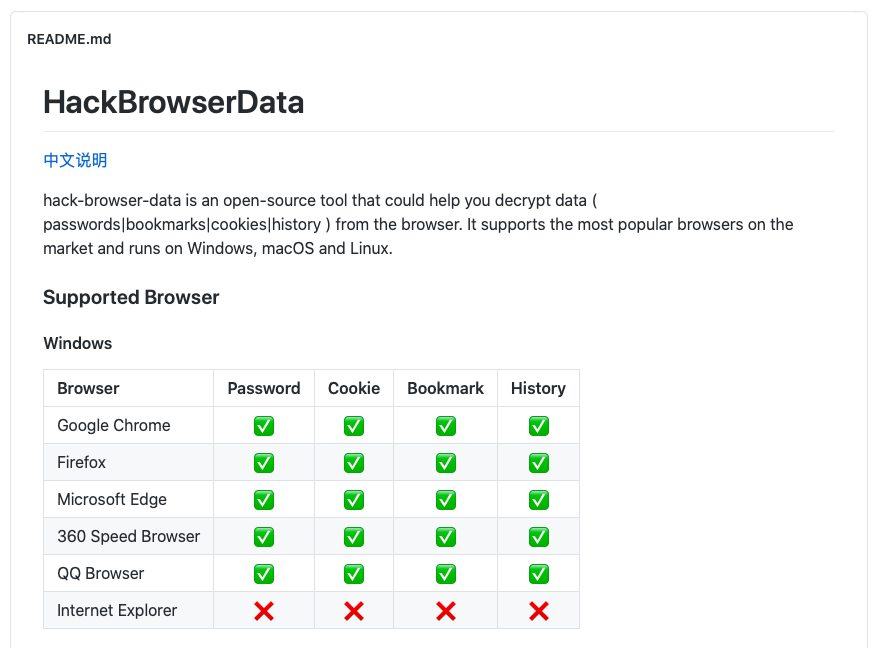
Decrypt passwords/cookies/history/bookmarks from the browser
Our extension does not reveal this attack surface.
-
UI
Sean Cassidy demonstrated a Pixel-perfect Phishing technology to steal passwords in his blog LostPass.
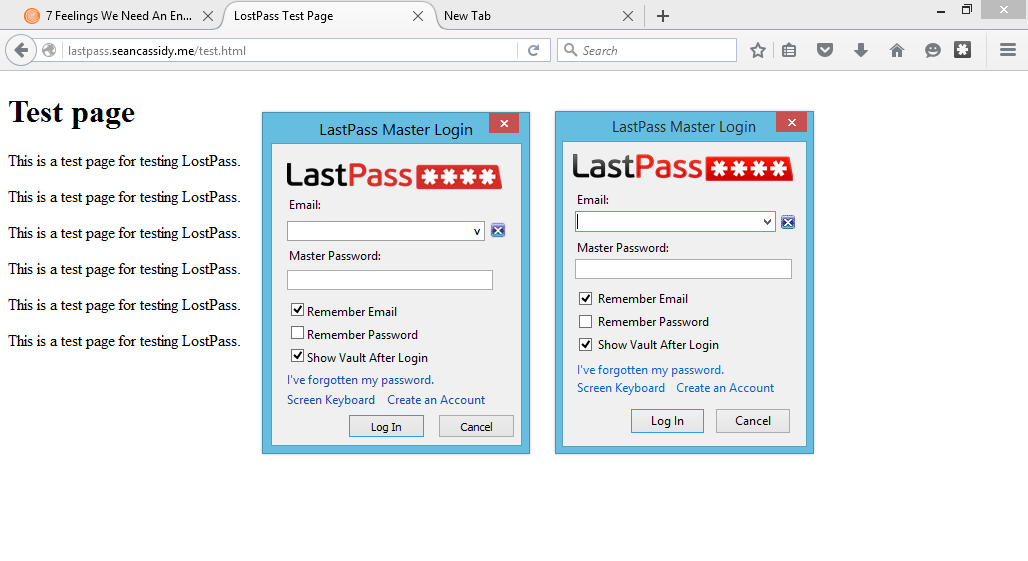
Phishing is usually attained by misdirecting users to enter their password into a spoofing UI faked by malicious programs. It is effortless to make a UI clone. Browsers do not offer much UI components for extensions to make them distinct from cloned UI. It is ironic:
Password managers can help prevent phishing, but cannot prevent being phished.
Our extension, like our app, has NO account, NO registration and NO login, so it has NOTHING to be phished.
-
Web DOM
This is a unique attack surface of browser extensions. We demonstrated how to steal passwords by manipulating UI of a password manager with the DOM API in the video at the beginning of this article. If there are some proper vulnerabilities can be used, it might be able to grab passwords with zero-click.
When using our extension, users need to scan QR code to fill password, so they must know what they are doing. Malicious programs can never attack the filling password without perception.
Summary
So how do we design a very secure autofill solution for desktop browsers? Let's put them together.
-
Passwords storage
The extension does not store passwords at all. All passwords are stored in ID Guard Offline app on the phone. It is a fourth generation password manager. Most security problems involve network. The app is still true offline, with no Internet permission. It does not expose the most dangerous attack surface. All saved passwords cannot be attacked from network at all.
-
Transportation
The account, to be filled into a desktop browser, is selected by the user on the phone. The username and password are encrypted and sent to the extension. The extension decrypts and fills them into the login form on the web page.
We introduce these methods to secure passwords during transportation.
- Encryption and decryption are managed in an isolated background process.
- Use strong ECC/ECDH algorithm to generate shared key to achieve end-to-end encryption.
- ECC private key is set to be non-extractable.
- ECC key pair is for one-time use only.
- Use strong
AES-256-GCMencryption, and prevent cipher text modification at the same time. - Use HTTPS/TLS for transportation.
- Limit ECC key pair validity to only 2 minutes.
As we know, HTTPS/TLS uses ECDH/AES to secure data in transit and is used by most cloud password managers for synchronization. The algorithm used in ID Guard Offline extension is more secure than HTTPS/TLS. We will explain it in our next post.
-
Phishing prevention
The Advanced Phishing Detection technology of ID Guard Offline app is the best among all known password managers. Our extension continues to invest in phishing detection too.
-
Autofill requires scan with phone manually.
Since Web DOM uncovers an uncontrollable attack surface, browser extensions can be attacked with the Web DOM API. In our design, passwords are stored on the phone, and only the selected account will be sent to the extension after scanning QR code manually. Malicious programs can never steal passwords from the app remotely without perception. Manual scan limits the speed of autofill. In one second, computer code can be executed as fast as to a million times, but no one can do scan more than once. Even supposing a user misbelieves the attacker and gives his/her password, this design still limits the quantity and speed of disclosure.
-
Request speed limitation
-
Advanced Phishing Detection of the app
After the QR code is scanned, users can see the filling website and its logo. If the selected password might be disclosed, the app can display a warning dialog. For example, if a user selects
facebookaccount to fill a phishing website, sayfaceb00k.com, the app will remind the user it is a phishing website. -
Warn users that passwords will be disclosed when submitting over HTTP connection.
-
Warn users that passwords can be disclosed when loading page over HTTP connection.
-
Warn users that if the main page is loaded over HTTP connection which is not safe. The login form can be hacked.
-
Warn users that passwords will be submitted to another website.
-
NOTE: malicious programs in the web page or bad extensions still can steal passwords filled in the login form by our extension. There is no prevention based on current web technology. Those bad programs can also steal passwords even if they are entered by user manually.
More articles about ID Guard Offline extension...
-
Stop using browser extension password managers. Use password manager extension instead.
Our ID Guard Offline designers are always taking security very seriously. We do not adopt common accepted but not good enough designs blindly.
-
Security design of ID Guard Offline extension
We all know that encrypted ≠ secured. Military encryption is more of a advertising slogan to fool
laymenlayperson. It is the security design that keeps passwords safe. -
End-to-end encryption is more secure than HTTPS
How secure? Better than HTTPS adopted by Internet banking.
-
How to verify extension design?
Two password managers Others ID Guard Offline Trustee The developer No one How do I know if you do what you say? Trust the developer. There are guide articles telling you how to verify them by yourself.