The Evolution of Password Manager (2/4)
TL;DR
The second generation password managers employ sophisticated algorithms to protect passwords with a master password. The master password is the key to unlock the vault.
In our previous post, the first generation password managers manage passwords, but not protect them well. As a gold mine gripping hackers, password managers must be revamped.
Since as early as about 2000, the second generation password managers emerged. They introduced a master password to encrypt the password databases. Password Safe(since 2002) and KeePass(since 2003) are two famous open source password managers with master password protection.
As discussed in our previous post, we know that,
encrypted ≠ secured
So how does the second generation protect data?
Cryptography Basics
In modern cryptography, encryption algorithms are well-designed. They are almost impossible to be cracked in the foreseeable future.
Encryption algorithms are divided into two categories, known as symmetric and asymmetric encryption. The former uses the same key to encrypt and decrypt data, while the latter uses two different keys, one for encryption and the other for decryption.
We will only discuss how symmetric encryption algorithms work in this article, since they are used by most password managers.
cipher = encrypt(key, plain)
plain = decrypt(key, cipher)
Here are the principles in cryptography:
- The algorithm cannot be kept in secret. Hackers know it.
- It is easy to recover
plainfromcipherwithkey, but very hard withoutkey. - The encryption
keymust be true random and be protected well.
At present, the most popular symmetric encryption algorithm is the Advanced Encryption Standard(AES). It comes in three flavors: 128-bit, 192-bit, and 256-bit. Among them, AES-256 is the most secure one and impossible to be cracked theoretically by today's technology. As the highest level algorithm, AES-256 is widely used in financial, military equipment and services, and also used by many password managers.
Some password managers claim to use "Military-Grade Encryption", which usually refers to the use of AES-256. "Military-Grade Encryption" is more of a marketing phrase. Timothy Quinn wrote that it should just be called “industry-standard encryption.”

As we already know, being encrypted does not necessarily mean being well protected. Therefore, password managers using AES-256 encryption cannot ensure that they are the most secure tools. Check the analysis in appendix to see how password managers failed to protect data well.
Key Derivation
Modern encryption algorithms are designed so well that most, if not all, hackers will not try to attack the algorithm itself. Instead, they try to obtain the encryption key. So protecting the encryption key is one of the most important things for password managers.
Generally, a master password cannot be used directly as an encryption key because it does not contain enough entropy. Even AES-128, the lowest one, requires at least 20 random symbols. Nobody can remember them!
Then, cryptographers develop Password-Based Key Derivation Function(PBKDF). These set of algorithms can transform a normal master password into a true random encryption key with proper size(128/192/256 bits) which can be used in AES.
It is magical, isn't it?

How does it work?
key = Hash(password, salt)
PBKDF algorithms introduce a salt which must be true random, and compute a hash from the master password, along with the salt. So even the master password is relatively simple, the derived key is good for encryption.
Currently, PBKDF2 is recmmended. Algorithms like bcrypt and scrypt are also used by some applications.
Encryption
How do the second generation password managers encrypt data? Let me explain more in detail.
-
Key derivation
graph TD MasterPassword & salt & count--> PBKDF2 -->|derive| key((key)) salt & count -->|save| KeyFile(KeyFile)When a user sets a master password, the password manager generates a true random salt and derives the encryption key from the master password with the salt. These are essentials for well-designed password managers.
- The encryption key is not persistent and only presented in the runtime memory.
- The salt is saved.
- The master password must never be saved, even in encrypted form. (This is an crucial rule, but lots of password managers violate it.)
It is so important that I'd like to emphasize it again. Master password must never be saved.
-
Encryption
graph TD key((key)) & plain & IV --> AES -->|encrypt| cipher cipher & IV -->|save| CipherFile(CipherFile)When saving passwords(the plain) into the vault, the password manager generates a true random initial vector(IV) and encrypts the password into cipher along with the encryption key. The cipher and IV are both saved.
-
Decryption
graph TD MasterPassword --> PBKDF2 KeyFile(KeyFile) -->|read| salt & count --> PBKDF2 PBKDF2 -->|derive| key((key)) CipherFile(CipherFile) -->|read| cipher & IV key & cipher & IV --> AES -->|decrypt| plain
When decrypting passwords from vault, user must enter master password first. Then the password manager,
- derives encryption key from the master password. (This time it reads the salt previously saved, rather than generates a new one.)
- decrypts data from cipher with the key derived just now along with the previously saved IV.
The above is the basic framework of how the second generation password managers protect data, though password managers may introduce minor modifications in practice. For example, a password manager uses unique encryption keys to protect each record and encrypts those keys with the key derived from master password.
In summary, there are 3 vital points in the second generation password managers.
- Derive encryption key from the master password with a PBKDF algorithm.
- Protect data with a strong symmetric encryption algorithm.
- Never save the master password, in any form.
Compared with the first generation, the second generation password managers provide good protection. And the only requirement is that using a strong master password which should be long and complex, and must not be disclosed to any other people.
Security of Master Password
The safety of the second generation password managers is reliant on master passwords. However, master passwords has some security issues in the real world.
-
Master passwords are not strong enough.
Lots of users do not realize that they should set a strong master password or do not know how to choose a strong one. (Fortunately, choosing a strong master password is not so difficult. Check this appendix How to choose a strong password
-
Master passwords can be disclosed unawares.
- Shoulder surfing.
- Recorded by IP cameras.
- Read by malicious app/input method on device.
- Or tell your girlfriend or not, when she demands it?
-
Master passwords are reused.
It is so difficult to remember passwords that people still reuse master passwords from app to app. However, reusing passwords is dangerous because it increases the chance of exposure and the password can be leaked by other Internet service sharing the same one.
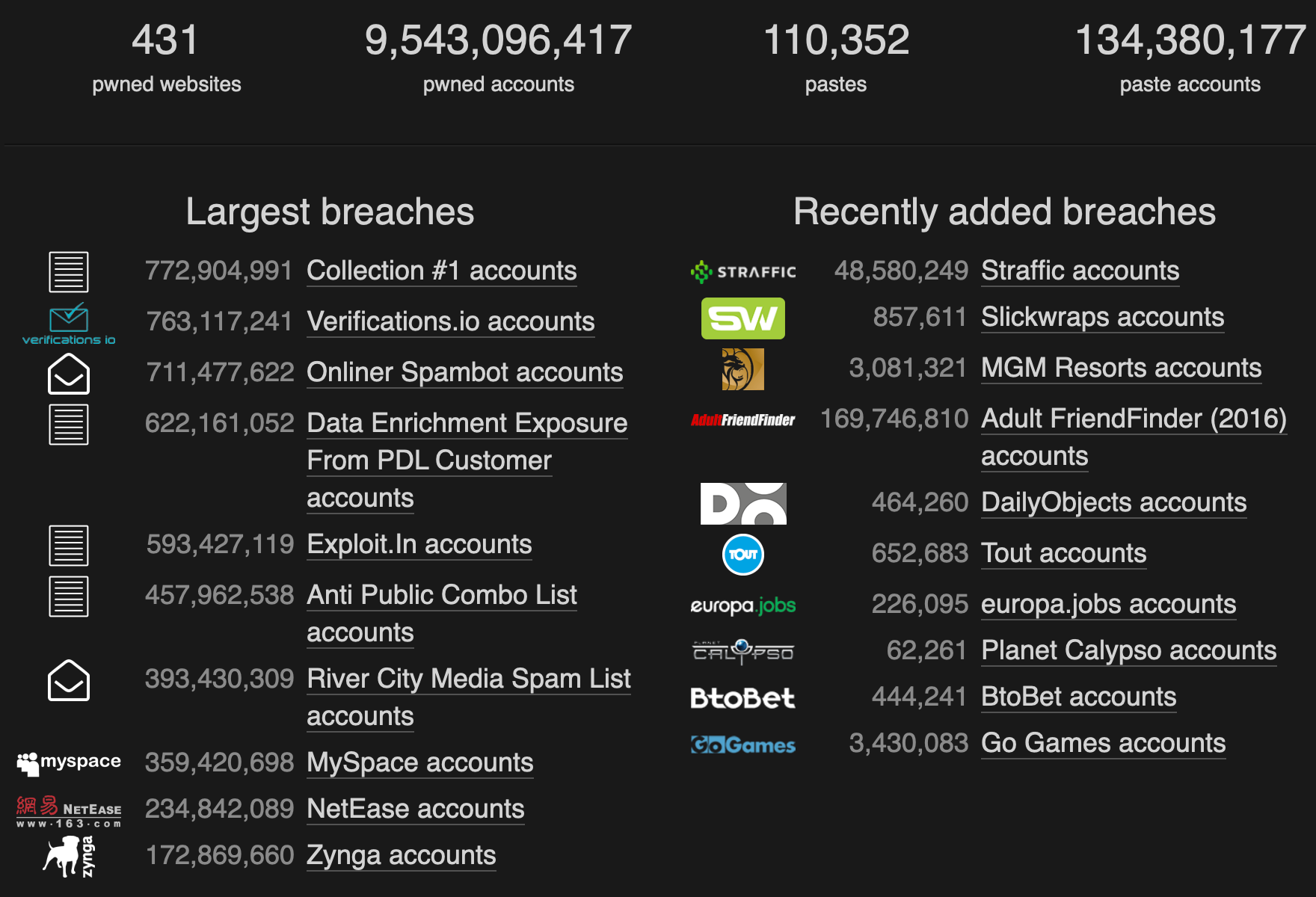
Is it real that passwords can be stolen from Internet services?
Definitely. Have I been pwned has collected more than 9.5 billion records, more than the population on this planet. The real total number is beyond our imagination since, you know, lots of breaches cannot be collected.
It is relatively not too hard to access password managers' vault. Plus once your master password is obtained by a hacker, all your passwords are in danger.
Continue to read
-
The Evolution of Password Manager (2/4)
Appendix