The Evolution of Password Manager (3/4)
TL;DR
The third generation password managers,
- introduce a master secret key to harden the vault on cloud side;
- are still reliant on master password on device side.
Previously, we discussed the second generation password managers protected by a master password. Cloud-based password managers expose a new attack surface on cloud side while synchronizing password vault to multiple devices via cloud service. Both hackers and bad employees might get access to the vault uploaded to the cloud. Your master password is your only bet, but it is far from unbreakable.
The third generation password managers come to save us. 1Password designed two-secret key derivation (2SKD) algorithm to solve those problems and published it in a white paper.
When a user sets up 1Password for the first time, 1Password generates a Secret Key, which is required to be saved by the user. Whenever setting up a new device, the user needs to import the Secret Key and enter master password. After finishing that, the Secret Key will be stored on device, so the user doesn’t need to import it every time he/she unlocks the app. There are 3 concepts here:
- Master password for unlocking app.
- Master secret key for setting up a new device.
- Encryption key for encrypting data.
Key Derivation Algorithm
graph TD
MasterPassword & SecretKey & count--> PBKDF -->|derive| key((key))
SecretKey & count -->|save| KeyFile(KeyFile)
Does it look familiar? Almost the same as the second generation except that SecretKey replaces salt.
If a developer changes a variable name, he/she does not change the app actually. So what is different?
SecretKey is not uploaded to the cloud.
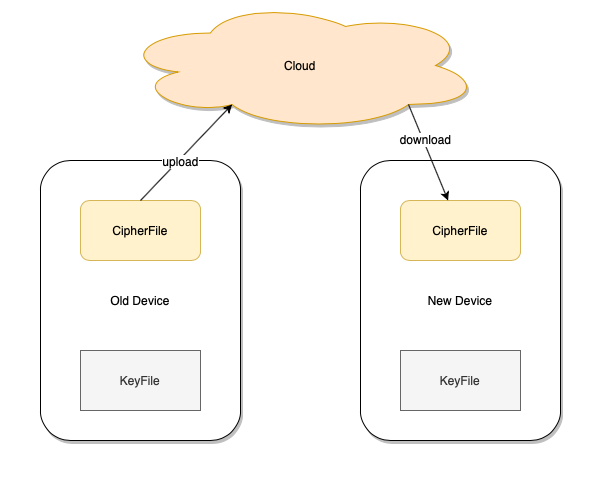
For cloud-based password managers, when signing in a second generation password manager on a new device, user enters the username and master password, then, the app can decrypt the vault downloaded from cloud. When signing in a third generation password manager on a new device, in addition to entering username and master password, user also needs to import the master secret key into the app.
It is a small change, but it makes a big difference. Hackers, either from inside or outside of the cloud provider, can no longer crack the encrypted vault. A true random master secret key is resistant to bruce force attack. Finally, password vault is safe in the cloud.
All in all, the third generation password managers protect password vault, in the cloud, with master password and master secret key, which is much safer than the second generation.
From the first to the third, each generation of password managers introduce a new factor to unlock the stored data.
| Generation | Unlock factors |
|---|---|
| first |
|
| second |
|
| third |
|
Security Issues
Though the third generation password managers can prevent passwords from being leaked on cloud side, it does not provide additional protection on device side. So, on device side, its security is at the same level as the second generation's.
The third generation password managers store master secret key and encrypted password database on disk. Because they cannot ask user to enter the long and complex random master secret key each time to unlock the app.
If a hacker gets access to the device, he/she may be able to steal the encrypted password database and the master secret key altogether. Just like the second generation, the third generation password managers come upon the same master password problem.
Cloud-based synchronization is convenient, but cloud has its dark side. Hackers may be able to crack lots of password vaults with the help of cloud computing even if they failed to grab the master password. Hundreds or thousands of powerful cloud servers can be assembled to beat those not-strong-enough master passwords, at relatively low cost.

Continue to read
-
The Evolution of Password Manager (2/4)
Appendix
-
The Evolution of Password Manager (3/4)