Are open-source password managers more secure? (2)
How do password managers protect our passwords?
Cryptography
Thousands of years ago, people started using codes and ciphers(cryptography) to protect secrets. Caesar cipher was one of the well-known classical ciphers, substituting one letter with another to encrypt a message.
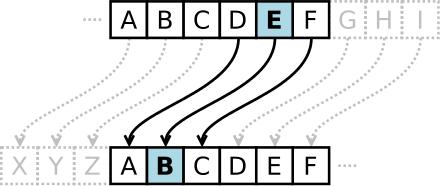
Classical ciphers can be easily broken by brute-force attack or frequency analysis. Think about it letter e is the most common in English, so the most common letter in the ciphertext is very likely the letter e.
In the late 20 century, modern cryptography became the cornerstone of computer security. Crypto algorithms transform plaintext to ciphertext with a key by a bunch of complex computations. It is impossible to recover the plaintext from the ciphertext without the key, even though we know the algorithms exactly.
Password managers, built on cryptography, usually encrypt our passwords with a user-set master password. We explained how the second generation password managers protect our data in The Evolution of Password Manager. This diagram shows the essentials.
graph LR MasterPassword([master password]) --> PBKDF2(PBKDF2) --> key --> Cipher(AES) plaintext([account data]) --> Cipher --> ciphtertext[[ciphtertext]]
master password, set and known only by the user.PBKDF2, Password-Based Key Derivation Function 2, the algorithm transforms themaster passwordinto an encryptionkey.key, derived from themaster passwordfor encryptionaccount data, plaintext to be encryptedAES, used by most password managers, is the marketed "military" algorithm, one of the most secure crypto algorithms.ciphertext, theencrypted databasesaved by the password manager.
By using PBKDF2 or other key deriving functions, the confidentiality of key changes to the non-divulgence of master password. It is like putting our passwords in a strongbox(encrypted database) and the master password is the key to the strongbox.
Common mistakes
There are quite a lot of password manager apps in the market. But some developers, including some famous security companies and long-established password manager companies, do not grasp the crypto algorithms well or are incapable of designing suitable security measures. In 2016, TeamSik found many vulnerabilities in password manager apps. Regarding passwords encryption, some common mistakes are:
-
Storing master password.
The master password should be unknown to anyone except the user. Storing the master password in plaintext or even ciphertext will increase the risk.
-
Using home-brewed crypto algorithms.
Developers must never write their own crypto algorithm, according to "Schneier's Law": Anyone, from the most clueless amateur to the best cryptographer, can create an algorithm that he himself can't break. It's not even hard. What is hard is creating an algorithm that no one else can break, even after years of analysis.
-
Using a hardcoded encryption key.
A hardcoded key is just like one key for all locks. That means everyone can unlock others' encrypted databases.
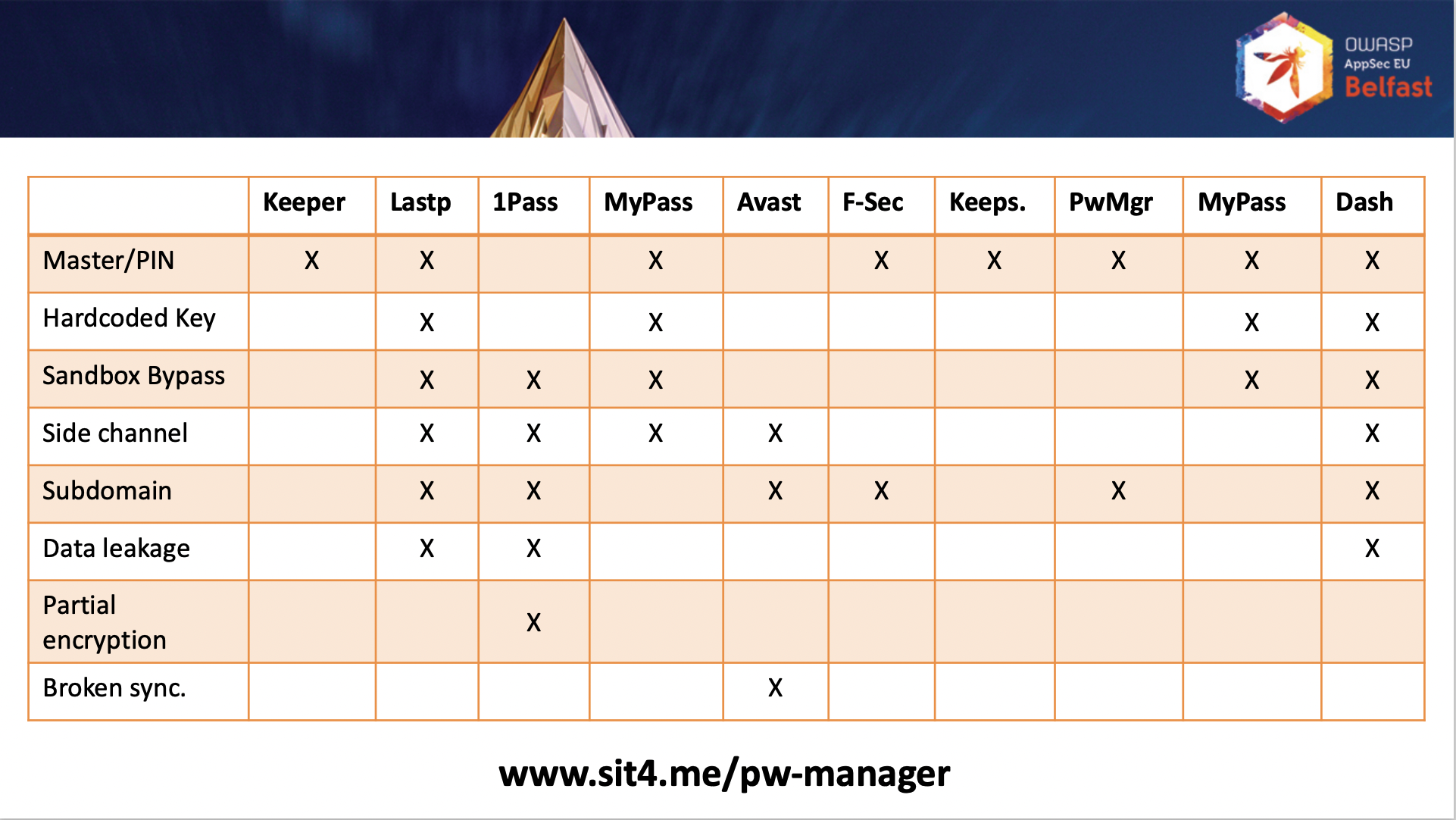
Many password managers stored master passwords or used home-brewed crypto algorithms as stated in the first row, Master/PIN, and some hardcoded encryption keys according to the second row(Other rows are irrelevant).
Users should look into the security design of password managers when choosing one. The big names are not necessarily better.
Open-source password managers can help users audit whether the cipher implementations are correct. And we explained the algorithms to help more developers do it right.
Unlock factors
As we know now, second-generation password managers require two factors to unlock, master password and encrypted database.
Many password managers tell users that data are safe if we keep the master password secure. However, it is still possible to leak it in the real world:
-
Using a short and simple master password for easy to remember and type.
-
Reusing the master password anyhow.
-
Disclosing to an insecure input method.
Many input methods will collect every tap when using them.
-
Recorded by powerful cameras far away!
Obviously, it is much safer to protect both the master password and the encrypted database.
Increasing unlock factors can improve security.
Though most password managers unlock with two factors, the master password and the encrypted database, KeePass can use a key file as the third factor, which helps significantly. We detailed how password managers increased security by using more unlock factors in The Evolution of Password Manager.
Some cloud-based password managers authenticate users by using 2FA. Since the second authentication factor is not for encryption, it is not a unlock factor mentioned in this article.
Threat models and attack surface
The more unlock factors, the more secure. Many password managers highlight the master password safety but neglect other unlock factors. Let's dig out the risks by analyzing threat models and attack surfaces.
Threat models are the potential risks of using a software. The threats or risks differ from person to person. Some might refuse to unlock their phones for their girlfriends, but others might share computers or even passwords on computers with family members.
How password managers protect our passwords and unlock factors varies considerably under different circumstances.
Social circles
Most desktop, browser extension, and web password managers keep the unlocked state long after entering the master password. People in social circles, family members, friends, or colleagues may touch your computer and find the saved passwords.
Mobile password managers are much safer since mobile phones usually lock automatically for a short time. Using biometric authentication is much easier than entering the master password.

Image by Peggy und Marco Lachmann-Anke from Pixabay
Threat mitigation:
- Does the password manager authenticate the user after idle?
Malicious programs intrusion
Password managers store the encrypted database on the hard drive on desktop computers. It has an attack surface. Most programs, including malicious programs, can access them easily. Some malicious programs can even hijack keyboard input and steal the master password. Some desktop password managers can utilize complicated technology to make it harder. But many browser-extension password managers can do nothing. They are popular but very insecure.
Password managers for smartphones are much safer. Android and iOS enable app sandboxing; one app cannot directly access another app's internal storage. So malicious apps cannot read the encrypted database inside password managers. However, Android allows apps to store data in external storage where password managers, such as many KeePass ports, do save the encrypted database. That exposes an attack surface for bad apps. Moreover, your master password can leak if entered with a bad input method. It can be more dangerous if the input method can access external storage(many of them can).
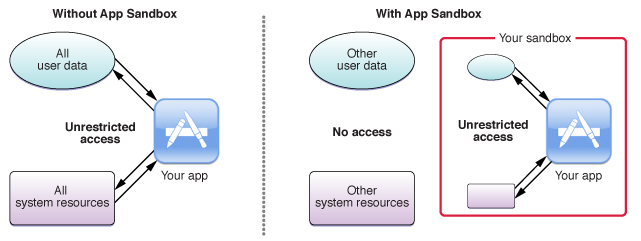
Threat mitigation:
- Does the desktop app mitigate keyboard hijack?
- Does the mobile app save the encrypted database on external storage?
There are always vulnerabilities in Operating Systems. Some can be abused by malicious programs to get system privileges and bypass the sandbox. In this case, they can steal encrypted databases inside the app's internal storage. We'd better install security updates in time.
Device loss
What if I lose my device? If a bad guy gets your device, he or she needs to unlock your device and then enter the master password to get your passwords. However, external storage is accessible via cable on some Android systems when locked. It is risky to save encrypted databases there.
Threat mitigation:
- Does the mobile app save the encrypted database on external storage?
To reduce risk, we should set complex or strong device PIN and master password.
Internet
Cloud-based password managers sync the encrypted database over the Internet. Even some offline password managers, such as Enpass, use the Internet too. When using the Internet, many threats are considerable:
-
Does the app send your passwords to the cloud?
Many apps collect user data while being used. Could the password manager collect our password intentionally or unintentionally? It increases the risk.

'The Social Dilemma' offers glimpse into surveillance capitalism -
Does the app upload the encrypted database to the cloud?
Uploading to the cloud is the service offered by cloud password managers. It's like giving your strongbox to some stranger, and you only have the key.
-
Does the app send your
master passwordto the cloud?For simplicity, many password managers use the
master passwordfor both encryption and authentication.Most Internet services send login passwords (like master passwords) to the cloud side to check if it is the same as the preset password. But password managers should never do this. They must verify the master password on the client side. The developers must carefully design the algorithm for authenticating the master password on the client side. Sadly, some developers do not acquire the skills and verify the password on the cloud, just like other services.
-
Does the app download multimedia data from the Internet?
Multimedia data are very complicated and hard to handle. Carefully constructed malicious data can break media libraries and control the app.

What are the ways to bypass NSO Group's Pegasus spyware?Pegasus, the notorious spyware which hacked thousands of politicians, journalists, activists, etc., developed by NSO Group, exploited vulnerabilities of multimedia libraries of OS and apps.
Many password managers download website logos from the Internet. Some even embed a browser to open any web pages inside the app. Actually, it CAN endanger passwords.
-
Do third-party libraries have the same risks?
Password managers, and all apps, are built on top of dozens of third-party libraries. Many of them talk to the Internet and present the same risks. Do they collect data? Do they send the encrypted database to the cloud? Do they download multimedia data from the Internet?
-
Web password managers.
Some cloud-based password managers offer web-based access. The web program is downloaded from the cloud by browsers and executed inside the browser. Malicious code can be easily injected by bad employees or inside hackers but is barely noticeable.
What's more, due to the browser's default behavior, your master password can be sent to the cloud side when failed to download the client-side authentication code on login.
As previously mentioned, web password managers have all the risks, including third-party, multimedia data, etc.
Users can hardly know what data apps send to and receive from the Internet. It is impossible to evaluate the risks.
Networking, a very opaque IO, discloses a huge attack surface. It is Pandora's box with every possibility.
Cloud
Cloud-based password managers store all users' encrypted databases on the cloud side. The cloud is a honey pot for Winnie and hackers. And there is also no guarantee that the inside employees, who have access to cloud data, will ever think about profiting from the data.

LastPass Hacked: How to Protect Yourself as Company Confirms Breach
Password manager companies can be hacked, just like other cloud services. If the encrypted databases get stolen, there is only one factor left to rescue -- the master password.
Conclusion
Crypto algorithms are marketed as "military" secure by many password managers. But it is only the cornerstone of confidentiality, and most password managers use the same AES crypto algorithm.
Some password manager developers, including some famous security companies with a good master of viruses, firewalls or VPNs, etc., do not know the data security technology. They cannot protect passwords well. Some even store master passwords, which is very wrong.
However, "military security" algorithms do not necessarily ensure data safety. The security design is much more critical. Besides the crypto algorithm, we should consider more on:
- How many unlock factors does it have?
- What threats does it mitigate?
- On facing these threats, what kind of attack surface and unlock factors are exposed?
To put it simply, the more unlock factors, the more secure. And each factor must be protected.
No password manager can meet all user requirements and mitigate all threats perfectly without any attack surface, without exposing any unlock factor. It is a paradox!
When choosing a password manager, we should figure out what threats we care about most. Ensure your password manager mitigates those threats with minimal attack surface and unlock factor exposure.
Open-source password managers give us a sight of the implementation. But we should focus more on its security design and ensure it minimizes the threats.
Previous: Are open-source password managers more secure? (1)