Trackers in password managers can threaten your passwords
March 17, 2021
➊ TL; DR
Third-party trackers integrated into password managers can access master password, vault, and decrypted password. The Internet access permission required by trackers makes the attack surface even larger. Security vulnerabilities, bad guys in the company, or hackers can steal passwords.
Recently, German security researcher Mike Kuketz wrote a blog, LastPass Android: Third-party providers monitor every step (LastPass Android: Drittanbieter überwachen jeden Schritt). It said, trackers in LastPass monitor every user interaction. And one of the trackers, Segment, says:
Collect every touch point
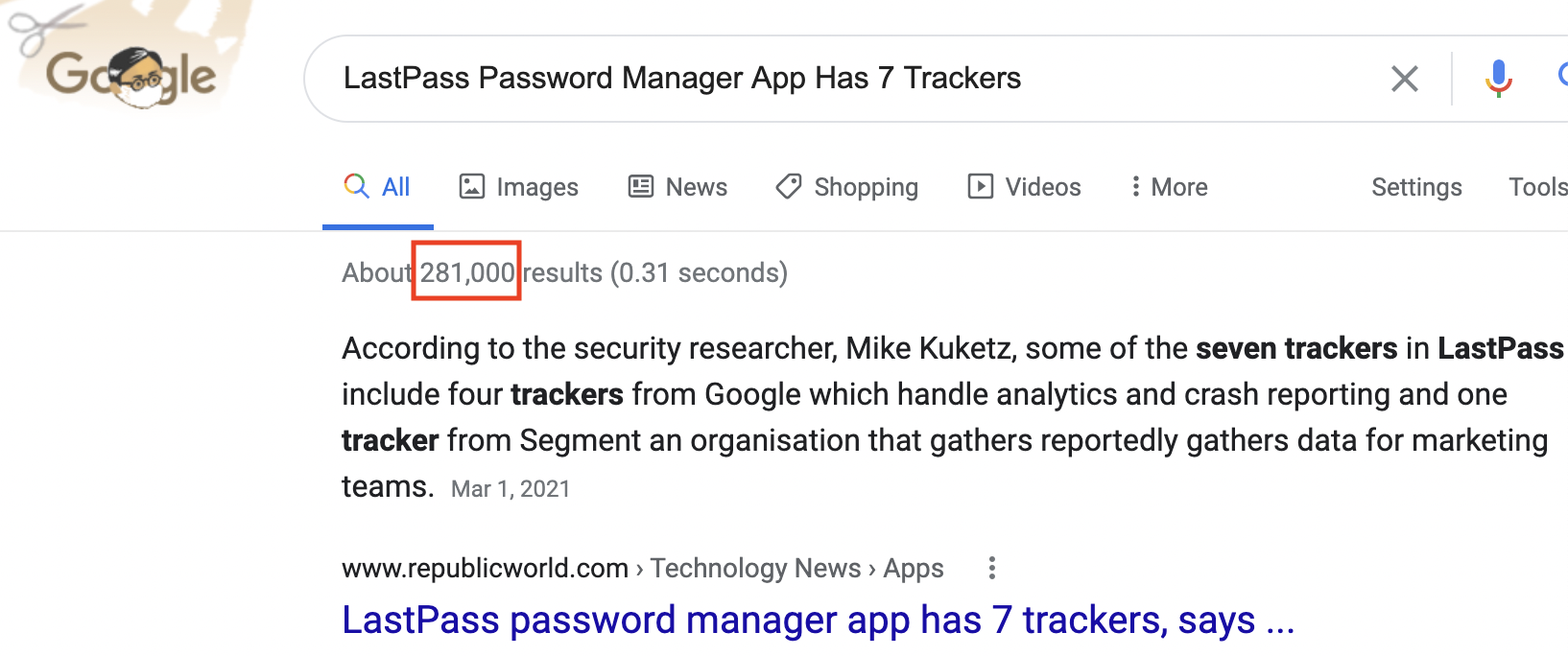
Tons of discussion after that. Google shows more than 280,000 results:
LastPass responded:
No sensitive personally identifiable user data or vault activity could be passed through these trackers. These trackers collect limited aggregated statistical data about how you use LastPass which is used to help us improve and optimize the product.
It is good to see that more research and more people are concern about the security of password managers. Password managers are security products, managing all passwords for users. Safety is extremely crucial.
They are much different than conventional apps.
So far, most discussions, if not all, focus on privacy issues, but few people worry about password safety.
Let me put the conclusion here and explain it later. **Trackers can endanger your passwords! **
Actually, Supply Chain Attacks increase very quickly in recent years. According to SolarWinds hack was 'largest and most sophisticated attack' ever: Microsoft president, up to 18,000 SolarWinds customers could have been compromised, including Microsoft, U.S. Treasury, Justice and Commerce departments and other agencies.
LastPass did not realize that third-party suppliers can threaten passwords managed inside their app.
For password managers, convenience is not crucial; defending various attacks is.
Now, let us disclose the risks of trackers step by step.
➋ Permission

App permission is what the Operating System allows an app to do, such as accessing the Internet, reading/writing public storage area, taking photos with the camera.
Modern smartphone OSes manage permissions by apps, not components/libraries inside apps.
What does that mean?
Trackers (or other third-party components) inside an app can do anything just like the app.
Reading runtime memory
Trackers inside apps can read any memory data of those apps when running, with no restriction, including the master password in the memory.
Reading files inside the sandbox
By introducing sandboxes for each app, iOS and Android can prevent bad apps from reading other apps' data inside their sandboxes. It is a considerable improvement for data security. However, it cannot stop trackers inside the app from accessing files inside their sandboxes, including the password vault.
Some password manager users think that the vault is OK to be exposed if keeping the master password safe.
Well, first, password managers must use cryptographic algorithms correctly. Password-Manager Apps said, TeamSIK broke some password managers successfully due to incorrect usage of crypto, and LastPass was one of them.
Also, keeping the master password safe is difficult. It can be disclosed in numerous ways:
- Bad programs can read it from memory directly.
- Bad input methods or keyloggers can steal it.
- Phishing.
- Bad programs can get it by recording screen.
- Password reuse.
- Shoulder surfing.
- Dictionary attack.
We have explained the unlock factors of password managers in our previous post The Evolution of Password Manager (4/4). Most password managers are the second generation. Once the vault is leaked, the master password is the only factor to guard all your passwords, while it might not be that safe.
| Generation | Unlock factors |
|---|---|
| first |
|
| second |
|
| third |
|
| fourth |
|
Full network access
Trackers need to send collected user data to the cloud. Network access is required. They can send data to the cloud, and at the same time, it is also possible that the cloud can send them instructions to execute.
➌ Threats
Well, what are the threats by using third-party trackers?
Vulnerabilities
Trackers are far from perfect. They can have security vulnerabilities. Once hackers exploit them, the corresponding permissions can also be exerted, including reading the master password from memory, uploading vault, etc.
Mostly, developers do not harden trackers for password managers. They are unlikely to know the security requirements. Let alone extra cost for training and development.
Insider threats
A few months ago, Ex-Cisco Employee Convicted for Deleting 16K Webex Accounts.
he deployed a code from his Google Cloud Project account, which automatically deleted 456 virtual machines that host the WebEx Teams application.

It is easier to compromise the service from the inside!
Hackers
If hackers break into the companies of trackers, they can initialize attacks, just like internal employees.
Usually, password manager companies are necessitated to do everything to prevent intrusion, both on the cloud and the app side, and to make it difficult to steal passwords even hackers are inside.
Tracker companies barely do as password manager companies. They do not know how password managers protect passwords or improve their skills to secure passwords. Their security processes are not as strict as password manager companies. They will not pay for the extra cost either.
Password manager companies do not have control or transparency to tracker companies. They do not know what tracker companies have done for security, nor audit trackers source code, let alone interfere with their security process.
➍ Attack
This article discloses the attack frameworks, not the attacking skills or code.
Steal with malicious code
Bad employees or hackers may insert malicious code into the tracker library before an update. This is how the SolarWinds hack happened:
Since system UI components usually cache the master password, the app is not easy to erase the master password from memory. Thus, malicious code can read the master password.
Many password managers decrypt all stored passwords in memory after unlocking, and malicious code in trackers can access them too.
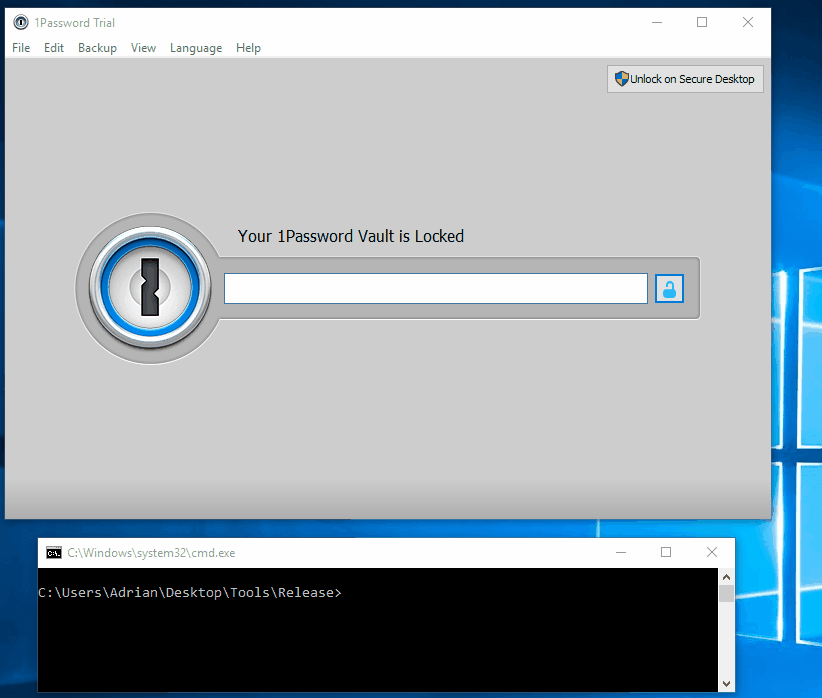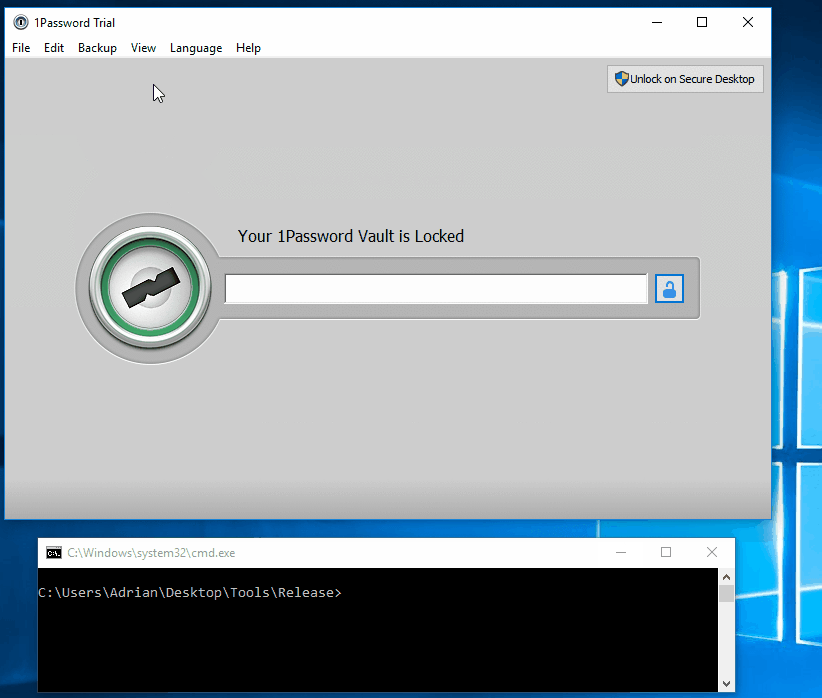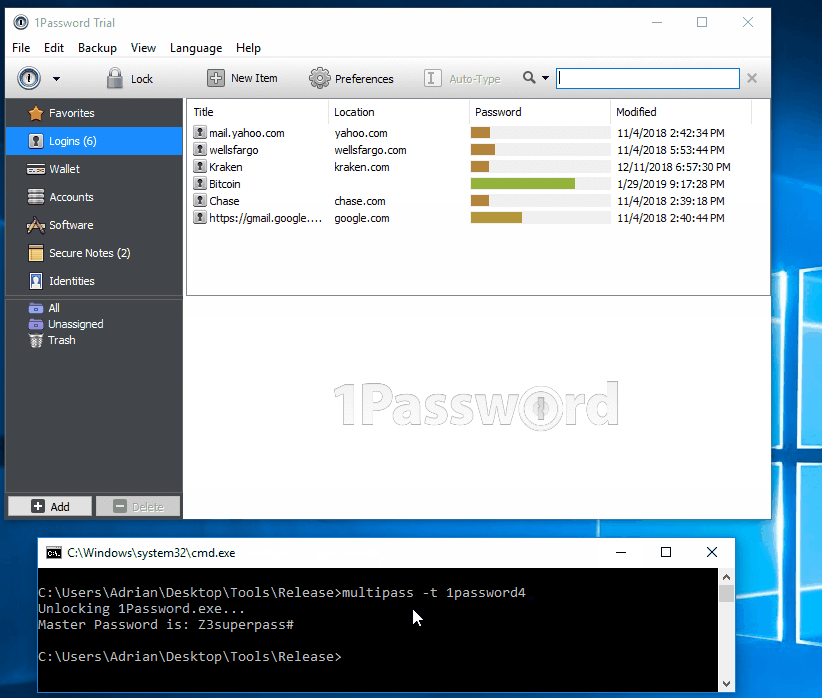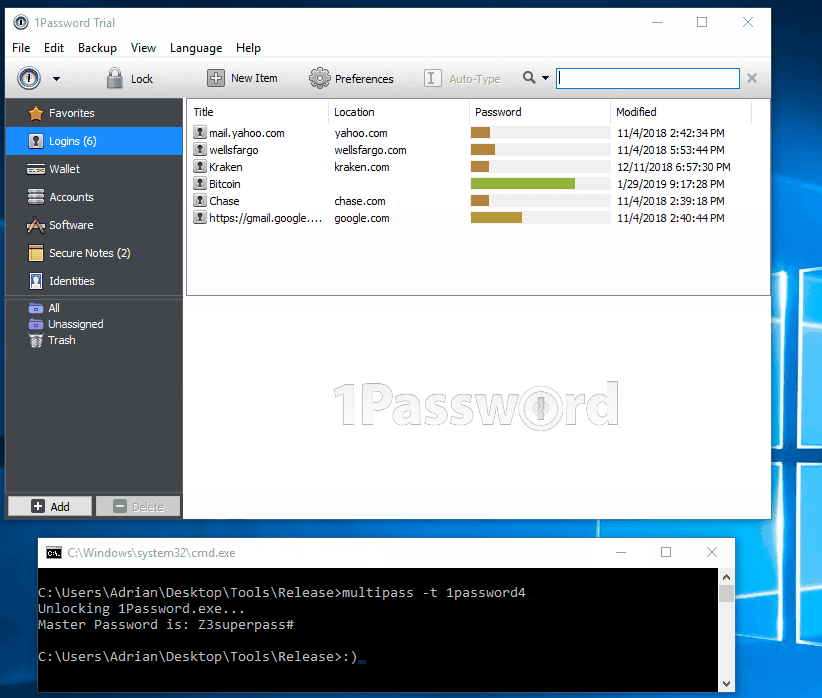
ISE extracted master password: Password Managers: Under the Hood of Secrets Management
BTW: Many password managers collect crash data to improve the product, even via third-party services. The crash data may include runtime memory (heap dump). It is another way to disclose the master password.
Malicious code can send the master password and the vault to a cloud server controlled by the bad guy. Then it is trivial to decrypt all the passwords.
Phishing master password
Malicious code in trackers can forge a lock UI to ask for the master password. It is different from ordinary phishing. It is impossible to know whether it is presented by trackers or the main app. Because the app starts those trackers inside.
Remote attack via hot code swapping
Frameworks like React Native, or Lua which is popular in gaming industry, can help apps load code from the cloud to do things that are not bundled in. Though both Apple and Google forbid apps to load code from the cloud to change their functionality, it is a just review requirement, not a technology limitation that is currently not available.
If the app passes the app store's review, there are many ways to load code over the Internet. Loading code from the cloud to read memory and files is trivial.
➎ Conclusion
Trackers use Internet permission to send collected user data to the cloud. As we know, most security incidents are involved with the network. The network is the single largest attack surface.
Grant Internet permission to a password manager is already risky! Even if the app and integrated trackers are OK, it is still possible to be hacked by downloading nasty data due to the underlying system's bug. LastPass integrates up to seven uncontrollable third-party trackers. Well, you know the risk to your passwords.