Encryption defect in Apple's iPhone iCloud keychain
What is the iCloud keychain
Keychain is the password manager on Apple's computers, iPhones, and iPads. It helps users save and manage their passwords. When users enable iCloud for the keychain, the iCloud keychain can synchronize passwords across all devices and keep additional copies of the passwords simultaneously.
Almost all Apple users use the iCloud keychain since Apple enables the iCloud for keychain by default.
iCloud keychain encrypts passwords before uploading
As you might know, Google Chrome does not encrypt your passwords before uploading them to the cloud. Though Google claims they encrypt your passwords on the server side. However, Google keeps the encryption key; of course, Google(hackers break in) can view your passwords. The two-factor authentication introduced by Google cannot stop the server-side attack. Obviously, it is not what we love.
Apple has done it better. They cannot read your passwords according to the document Secure iCloud Keychain recovery, nor do hackers break in or FBI.
iCloud Keychain escrows users' keychain data with Apple without allowing Apple to read the passwords and other data it contains.
The user's keychain is encrypted using a strong passcode,
There are several ways to establish a strong passcode:
- If two-factor authentication is enabled for the user's account, the device passcode is used to recover an escrowed keychain.
- If two-factor authentication isn't set up, the user is asked to create an iCloud security code by providing a six-digit passcode. Alternatively, without two-factor authentication, users can specify their own, longer code, or they can let their devices create a cryptographically random code that they can record and keep on their own.
Let me give a simple explanation:
- iCloud keeps a copy of your passwords saved in the iCloud keychain, but Apple cannot read them.
- Your passwords are encrypted with a strong passcode.
- Apple uses your device passcode as the strong passcode.
Since the keychain encrypts your passwords with the iPhone passcode before uploading to iCloud, Apple cannot decrypt the cipher because Apple does not know your iPhone passcode.
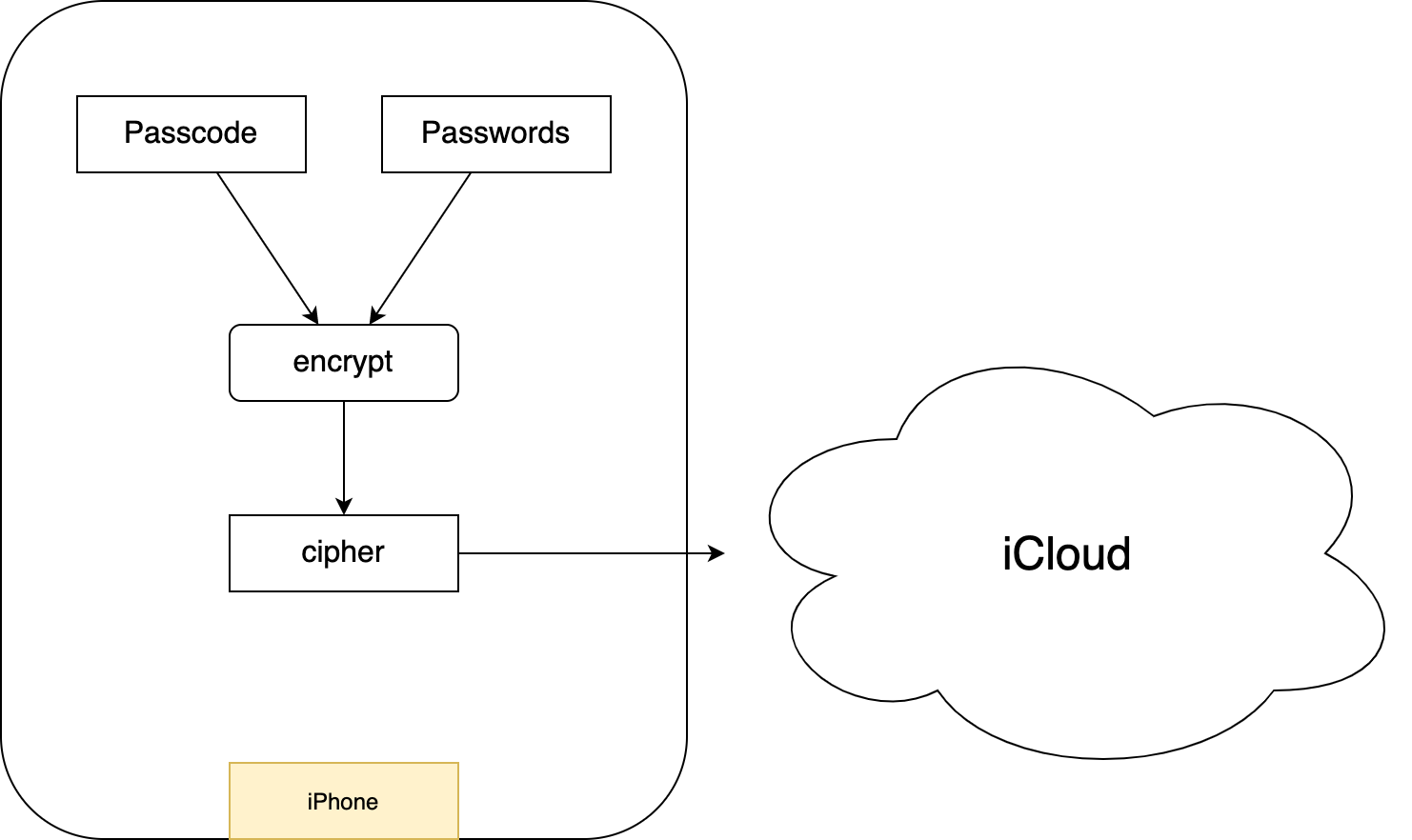
The decryption process is:
- Your new iPhone downloads the escrowed data from iCloud;
- enter the passcode of your previous iPhone;
- the keychain app on your new iPhone decrypts your passwords from the cipher.
But, how strong is the strong passcode?
Almost all iPhone users set a 6-digit passcode or even 4 digits. Apple uses these numbers to encrypt your passwords.
A-not-very-old story
The tech firm has been asked to help break into that phone, and they have refused to comply; the FBI has gotten a court order compelling them to do so. Apple has said it will fight the order and the Feds have accused the firm of prioritising its "public brand marketing strategy" over a terrorism investigation. -- Apple v the FBI: what's the beef, how did we get here and what's at stake?

A few years later, Apple gave the FBI access to the iCloud account of a protester accused of setting police cars on fire. Since iPhone uploads all data, including your passwords, to the iCloud by default, the FBI does not need to unlock iPhone anymore. It is much easier to crack data on iCloud.
The encryption is flawed
If the iCloud keychain encrypts passwords with only 6 digits, how long does it take to crack them? Let's make an estimation. Piece of cake!
- iPhone derives a key to encrypt data on unlocking with the passcode. It should not be long to keep the user waiting. Let's say it costs 500 ms.
Crypto algorithms cannot use the digital passcode directly. They use an encryption key that can be derived from the 6-digit password with algorithms like PBKDF2.
- 6-digit has only 1 million possible options.
- It costs 500,000 seconds, i.e., 139 hours, to derive all the possible keys.
Today, AMD's desktop CPU Ryzen Threadripper PRO 5995WX comes with 64 cores and 128 threads. It is much faster than a smartphone processor. It can crack the encryption within 1 hour. What about a GPU cluster? It can be done within a few minutes.
Now you know the encryption cannot stop Apple, the FBI, or hackers break into iCloud to crack your passwords saved in the iCloud keychain.
What mistake does Apple make
But we use 6-digit PIN(personal identification number) everywhere, electronic devices, bank cards, etc. Is it safe?
Yes, it is. The 6-digit PIN is for identifying a user. iPhone will disable for 1 minute after 6 failed passcode attempts in a row. It will disable longer and longer with more incorrect attempts. So bad guys can never try 1000 times to unlock your iPhone.
The mistake is that the PIN is for identification, not encryption. However, Apple violates the rule.
At last, we hope Apple makes the document more precisely:
iCloud Keychain escrows users' keychain data with Apple without allowing Apple to read the passwords and other data it contains easily.
After all, it takes a few minutes.